Attack Surface Management (ASM):
Minimize Your Threat Landscape
to Harden Your Digital Perimeter
Attack surface management involves the systematic identification, analysis, and reduction of potential entry points and vulnerabilities within an organization’s infrastructure and systems. This service comprehensively assesses and minimizes your attack surface to we improve overall security posture, minimize the avenues available to attackers, and eliminate vulnerabilities.
“Gartner identifies attack surface expansion as a top security and risk management trend.”
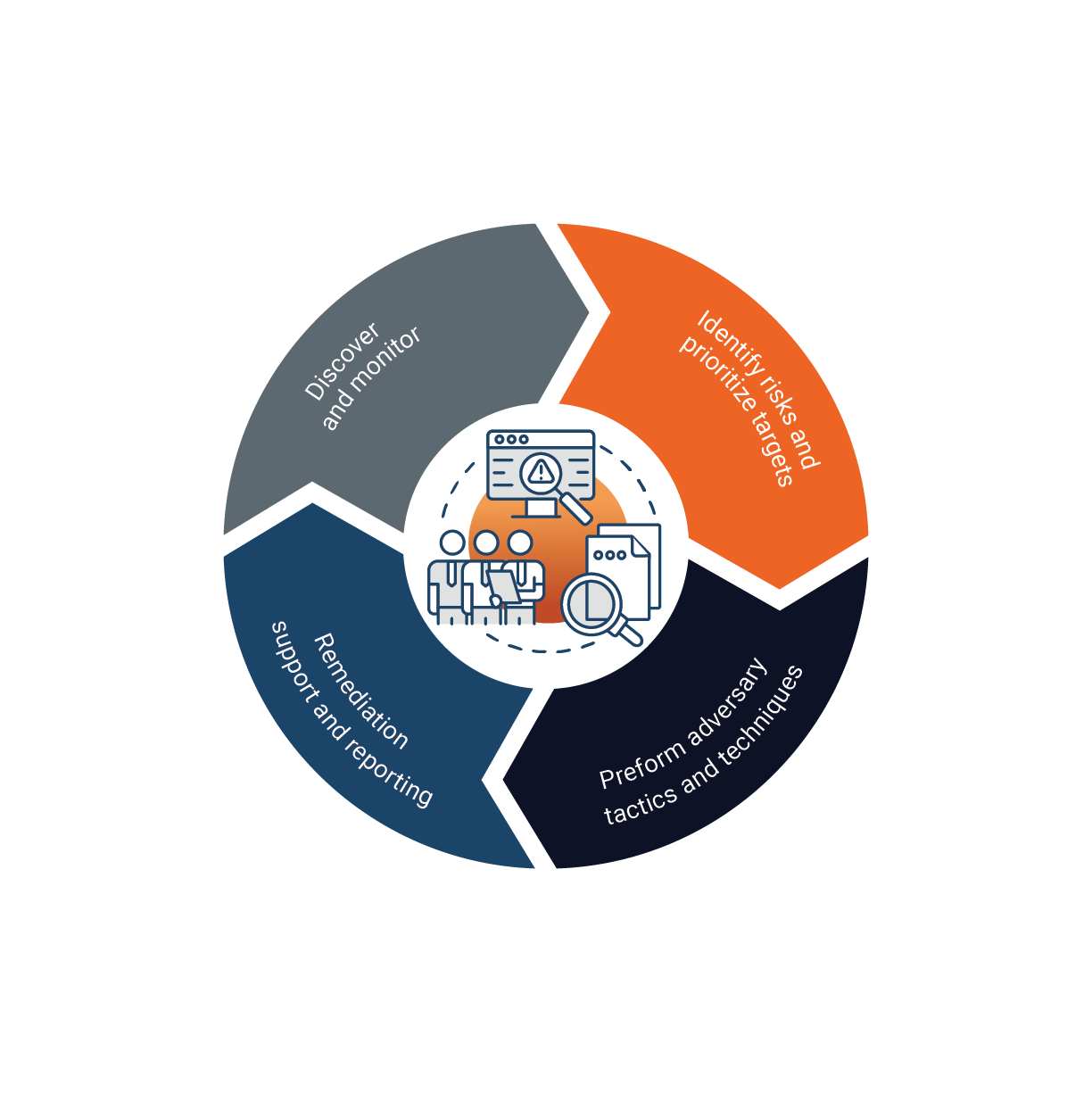
Client Challenge
Identify Your External Risks
Attack surface management is critical, high-impact security operations practice that delivers the following benefits
Risk Reduction. Identifies and minimizes the attack surface to broadly reduce exposure to cyberthreats. ASM mitigates vulnerabilities by minimizing potential entry points and significantly decreasing the likelihood of a successful attack.
Security Posture Improvement. Effective attack surface management contributes to an organization’s overall security posture by strengthening defenses, improving resilience, and ensuring that security measures align with industry best practices.
Proactive Response. ASM is a proactive approach that identifies potential vulnerabilities and weakness before they can be exploited or leveraged for malicious purposes.
Align with Compliance Requirements. Many industry regulations and compliance frameworks require organizations to maintain a strong security posture and protect against potential threats. ASM helps organizations meet these requirements by actively reducing vulnerabilities and ensuring adherence to security standards.
Protect Critical Assets. By minimizing the attack surface, organizations can better protect their critical assets, including sensitive data, intellectual property, customer information, and operational systems. ASM reduces the likelihood of unauthorized access, data breaches, and potential financial or reputational damage.
Third-Party Risk Management. ASM also extends to assessing and managing the security risks associated with third-party vendors and partners. It helps organizations understand and mitigate potential vulnerabilities introduced through external connections and dependencies.
EMBER’S ATTACK SURFACE
MANAGEMENT SERVICES
ASM requires the coordination of several key activities including
Inventory and Discovery
Identifying and cataloging all assets, systems, applications, and network components within an organization's environment.
Asset Profiling
Understanding the purpose, functionality, and interdependencies of each asset to determine its potential risk and impact if compromised.
Vulnerability Assessment
Conducting regular vulnerability assessments and penetration testing to identify weaknesses and vulnerabilities in the organization's assets and systems.
Configuration Management
Ensuring that systems and applications are properly configured and hardened to reduce the attack surface.
Security Controls
Implementing a range of security controls and measures to protect critical assets and systems. This may involve deploying firewalls, intrusion detection systems (IDS), antivirus software, encryption, multi-factor authentication (MFA), and other security technologies.
Third-Party Risk Management
Assessing and managing the security risks associated with third-party vendors and partners that have access to the organization's systems or data.
How EMBER’s
ASM Works
EMBER employs several best-in-class security tools to monitor and protect your attack surface, including
1
Persistent Vulnerability Management (PVM)
PVM delivers continuous visibility within your IT systems, rapid incident response to potential threats, increased uptime, and improved overall performance. PVM helps keep your organization up-to-date and secure — and one step ahead of hackers.
2
Threat & Vulnerability
Management (TVM)
TVM provides insights into your organization’s vulnerabilities and security posture and a proactive means to identify and address gaps in your security — before an attack.
Tools We Use to Deliver ASM
EMBER IT Services —
Security How You Need It
Building and maintaining an effective security infrastructure is expensive and time-consuming. Hiring and keeping top security talent is an ongoing challenge, and procuring and upgrading security solutions can wreak havoc on your capital budget.
EMBER offers a full range of services and solutions designed to protect your data, employees, and environment. These solutions are constantly evolving to meet new threats, scale quickly, and can dramatically reduce your capital spending.
Our team possesses an extensive IT background and employs best-in-class partners, tools, and methods. By combining our tactical expertise with security orchestration and automation, EMBER delivers unparalleled speed and responsiveness, keeping your organization safe and letting you focus on your core business.
Talk to an expert
Learn how EMBER’s ASM Solution can reduce the risk of debilitating cyber attacks.